What is ARP Spoofing and how does it work?
Firewalls, proxy servers, demilitarized zones (DMZ) – companies are increasingly deploying tactics like these to protect their private networks from the dangers of the internet. But not all attacks come from the outside. The weakest link in the chain of network security is the Local Area Network (LAN). An attacker who is already inside the network has countless ways available to them to view data traffic and manipulate it at will. Internal attackers use the vulnerability of the ARP protocols. This is used with the IPv4-based Ethernet networks to resolve IP addresses to MAC addresses, presenting security problems to administrators.
ARP entries can easily be manipulated using falsified data packets. These cases are referred to using the term ARP spoofing, a man-in-the-middle attack that enables hackers to switch unnoticed between two communicating systems. Here we show how the address resolution can be specifically manipulated via ARP and suggest possible countermeasures.
ARP spoofing (also known as ARP poisoning) describes man-in-the-middle attacks carried out on local network ARP tables. This form of attack results in hackers sending out fake ARP packets that slide in between two communicating systems unnoticed so they can listen to or manipulate their data traffic.
ARP: Addressing in the LAN
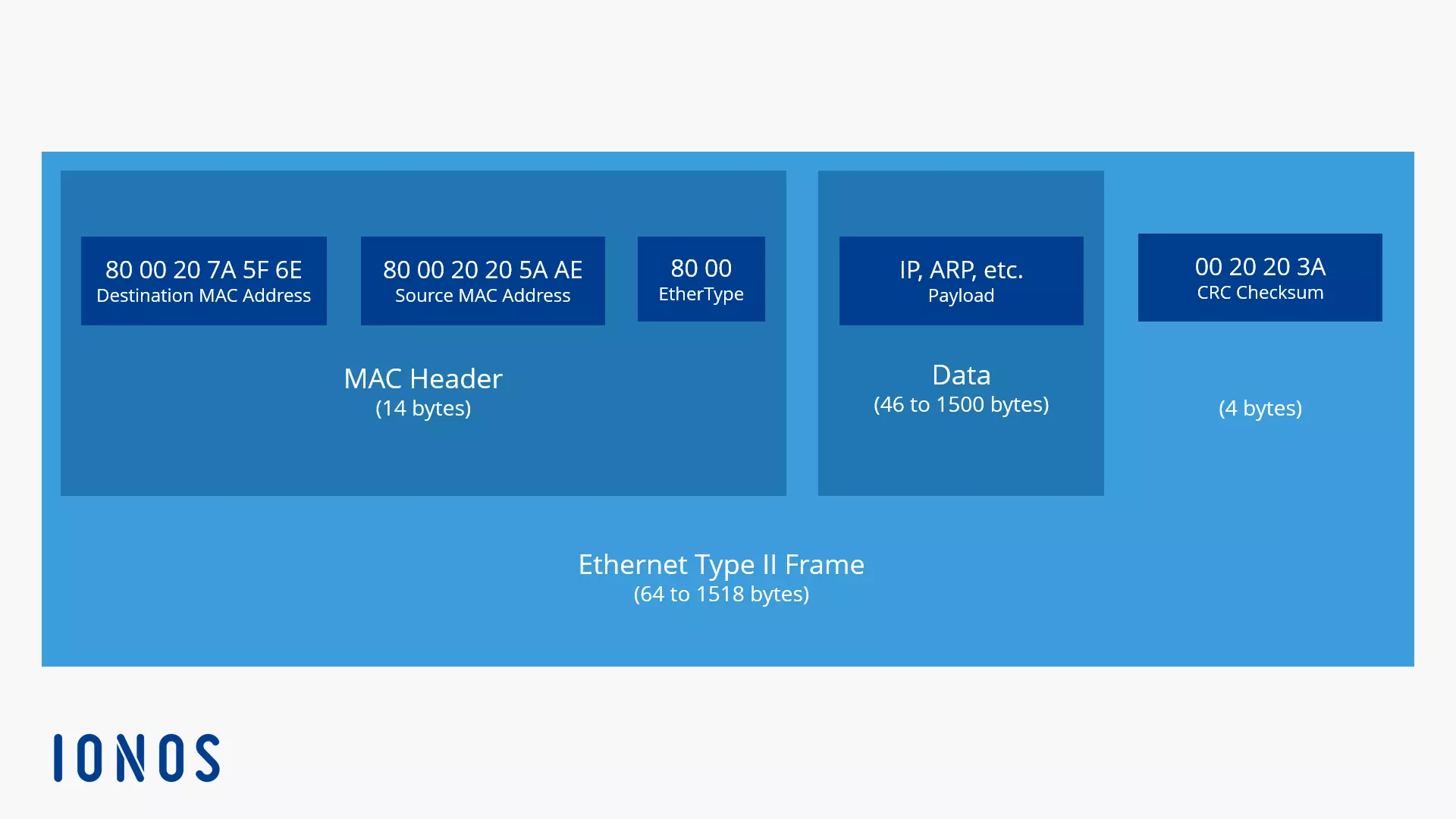
Unlike devices on the internet, devices in the LAN don’t communicate directly via IP addresses. Instead, they use physical hardware addresses for addressing in local IPv4 networks. These MAC addresses (Media Access Control) are unique 48-bit numbers, and make it possible to identify each device in the LAN via its network card.
Example of a MAC address: 00-80-41-ae-fd-7e
MAC addresses are assigned by their respective hardware manufacturers and are unique worldwide. Theoretically, these hardware addresses would be suitable for global addressing. But in practice, this doesn’t work because IPv4 addresses are too short to completely map the MAC address. In networks based on IPv4 the address resolution via ARP is unavoidable.
If Computer A wants to contact Computer B within the same network, it must first determine the appropriate MAC address for its IP address. This uses the Address Resolution Protocol (ARP), a network protocol that operates according to the request response scheme.
After searching for the appropriate MAC address, Computer A sends a broadcast request (or ARP request) to all devices on the network. This request contains the following information:
A computer with the MAC address xx-xx-xx-xx-xx-xx and the IP address yyy.yyy.yyy.yyy would like to get in contact with a computer with the IP address zzz.zzz.zzz.zzz and requires the appropriate MAC address.
The ARP request is received by all computers in the LAN. In order to prevent an ARP request from being submitted prior to the sending of each data packet, every computer in the network performs a local table, called the ARP cache. In these tables, all known MAC addresses are temporarily stored along with their matching IP addresses.
In this way, all computers in the network record the broadcast request along with the accompanying sender address. An answer to the broadcast request is only expected from Computer B. Its ARP reply contains the following information:
This is the system with the IP address zzz.zzz.zzz.zzz. The requested MAC address is aa-aa-aa-aa-aa-aa.
If this ARP reply is delivered to Computer A, then it has all of the information required to send data packets to Computer B. Communication over the local network is now not prevented by anything.
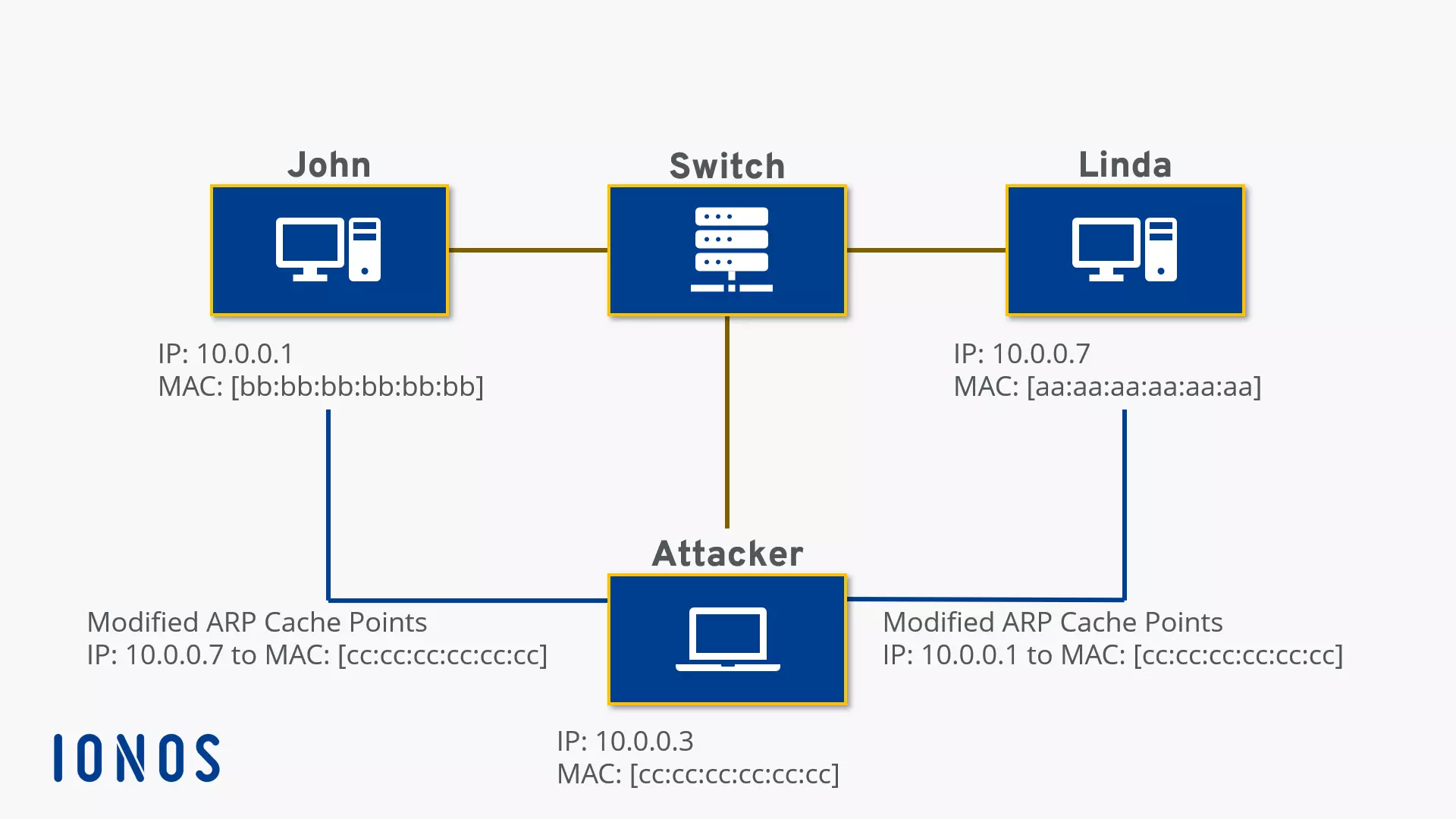
What then, if the intended computer doesn’t reply, but instead the reply comes from another device controlled by an internal attacker with criminal intentions? This is where ARP spoofing comes into play.
What is ARP spoofing?
The request response scheme of ARP protocols is arranged so that the first answer to an ARP request is accepted and stored. In the context of ARP spoofing, hackers try to preempt the actual target computer in order to send a reply packet with incorrect information and manipulate the ARP table of the inquiring computer. This is referred to as ARP poisoning, or a “contamination” of the ARP caches. As a rule, these data packets contain the MAC address of a network device being controlled by hackers. The targeted system then links the output IP to the wrong hardware address and sends all future data packets to the hacker-controlled system. This system now has the opportunity to record or manipulate all data traffic.
To remain undetected, the intercepted data traffic is usually passed on to the actual target system. A hacker then becomes a man in the middle. If the intercepted data packets are not forwarded, but are instead discarded, ARP spoofing can result in a denial of service (DoS). ARP spoofing functions both in LAN and WLAN environments. Even the encryption of wireless networks via Wi-Fi Protected Access (WPA) offers no protection. In order to communicate in local IPv4 networks, all connected devices must resolve MAC addresses – which can only be done via ARP.
One well-known software that lurks specifically on broadcast requests and responds with fake ARP replies is Cain&Abel. But to ‘contaminate’ the ARP cache of a network device, a hacker doesn’t necessarily need to wait on ARP requests. Another strategy includes continually bombarding the network with false ARP replies. While most systems ignore answer packets that can’t be assigned to a request, this changes as soon as a computer in the LAN starts an ARP request and so is willing to receive a response. Depending on timing, either the response of the target system or one of the fake response packets will arrive at the sender first. This attack pattern can be automated by programs such as Ettercap.
ARP attack software at a glance
Programs that operate in the framework of ARP spoofing as hacking software are usually presented as security tools and are available for free online. Administrators can use the programs to test their network and protect against common attack patterns. The most common applications are ARP0c/WCI, Arpoison, Cain&Abel, Dsniff, Ettercap, FaceNiff, and NetCut.
- ARP0c/WCI: According to the provider, ARP0c/WCI is a tool that uses ARP spoofing to intercept connections in a private network. To do this, the software sends false ARP response packets, which redirect traffic to the system running ARP0c/WCI. The integrated bridging engine is used to forward information to the actual target system. Packets that aren’t delivered locally are forwarded by ARP0c/WCI to the appropriate router. A man-in-the-middle attack generally remains undetected. The program is available for both Linux and Windows and can be downloaded free of charge on the provider’s website.
- Arpoison: The command line tool Arpoison generates user-defined ARP packets, in which the user can set the sender and target addresses. Arpoison can be used for network analysis, but is also used as an attack software. The tool is available for free and operated under the GNU license.
- Cain&Abel: The Cain&Abel program, developed as an old password recovery tool, makes it possible to intercept networks and decrypt their encrypted passwords. Since version 2.5, the software also contains ARP poisoning functions that intercept IP traffic in the switched LANs. Even SSH and HTTPS connections are no hurdle for Cain&Abel. In order to analyze WLAN network traffic, the program has supported the AirPcap adapter since version 4.0, which enables the passive reading of data traffic in the WLAN. Attacks against WPA-secured wireless networks have been possible since version 4.9.1.
- Dsniff: Dsniff is a collection of programs that provide a variety of tools for network analysis and penetration tests: with Dsniff, Filesnarf, Mailsnarf, Msgsnarf, Urlsnarf, and Webspy it’s possible to spy on networks and intercept data, emails, or passwords. Arpspoof, Dnsspoof, and Macof make it possible to detect data that’s normally not accessible in switched networks. Man-in-the-middle attacks on SSH and SSL/TLS secured connections can be implemented through SShmitm and Webmitm programs.
- Ettercap: The user-friendly APR spoofing tool Ettercap is primarily used for man-in-the-middle attacks. The software supports diverse Linux distributions as well as Max OS X (Snow Leopard and Lion). A Windows installation is possible, but requires additional settings. In addition to the user interface, the ncurses front-end and the GTK2 GUI graphical user interfaces are available. Actions such as Sniffing, ARP attacking, and collection of passwords can be automated. Ettercap can manipulate intercepted data and attack connections that are secured via SSH or SSL. The program is officially offered as security software and is used in product testing.
- FaceNiff: The Android app FaceNiff allows users to read session cookies in WLAN networks and to take offer sessions. Hackers utilize the tool in order to hack into Facebook, Amazon, or Twitter accounts, so it doesn’t matter whether the wireless network is freely available or encrypted via WEP, WPA-PSK, or WPA2-PSK. A reliable protection against FaceNiff can be found in authentication protocol EAP (Extensible Authentication Protocol) such as SSL. The Android software is based on the Firefox extension Firesheep and can be used on smartphones in combination with the previously installed standard browser.
- NetCut: With the network management software NetCut, administrators can manage their network on the basis of ARP. The tool detects all devices connected to the network and outputs their MAC addresses. A simple click on one of the listed addresses is enough to disconnect the device from the network. NetCut is particularly suitable for DoS attacks, provided the attacker is on the same network as the victim; man-in-the-middle attacks cannot be implemented with this software.
ARP spoofing and encryption
If a hacker succeeds in switching between two communication partners, they have free rein over the unprotected connections. Because the entire communication of a hacked connection runs through the system of the hacker, they can read and manipulate the data at will. Protection against data espionage can be promised by some encryption techniques and certificates for authentication. If an attacker only catches encoded data, the worst case is limited to a denial of service by discarding data packets. But reliable data encryption has to be implemented consistently.
Numerous tools that can be used for the purpose of man-in-the-middle attacks provide ARP spoofing functions as well as client and server implementation for SSL/TLS, SSH and other encryption protocols. These have the ability to imitate appropriate certificates and establish encrypted connections. Cain&Abel, for example, simulates a SSL-capable webserver, which then sends an untrustworthy SSL-certificate to the victim system. Admittedly, network users are warned in this case, but these warnings are usually either ignored or misinterpreted by the user, so lessons on the subject of network security should also cover the responsible handling of digital certificates.
Counter-measures
Since ARP spoofing exploits the address resolution protocol, all IPv4 networks are prone to attacks of this kind. The implementation of IPv6 was also unable to solve this core problem. The new IP standard renounces ARP and instead controls address resolution in the LAN via NDP (Neighbor Discovery Protocol), which is also vulnerable to spoofing attacks. The security gap could be closed through the Secure Neighbor Discovery (SEND) protocol, but this isn’t supported by many desktop operating systems.
Possible protection from the manipulation of ARP caches is offered by static ARP entries, which can be set in Windows, for example, by using the command line program ARP and the command arp –s. But since entries of this type have to be made manually, these security methods are generally restricted to only the most important systems in the network.
A further measure against the abuse of ARP is the division of networks into Layer 3 switches. Uncontrolled, broadcast requests reach only the systems that are in the same network segment. ARP requests in other segments are checked by the switch. If they work on the network layer (Layer 3) then the IP address is matched with both the MAC address and the previous entries. If there are any discrepancies or frequent reassignments, the switch alarm will sound. But the required hardware is quite expensive. Administrators have to gauge whether the boost in security justifies the financial expense. On the other hand, the significantly more favorable Layer 2 switches that work on the data link layer are not adequate. Although they register a change in the MAC address, the assignment to the respective IP address remains unaffected.
Numerous software manufacturers offer monitoring programs that can supervise networks and detect suspicious ARP processes. Well-known tools are the open-source software Arpwatch, as well as ARP-Guard and XArp. In addition, intrusion detection systems such as Snort can be used to monitor address resolution via ARP.
- Arpwatch: If the cross-platform open-source tool Arpwatch is integrated into a local IPv4 network, it continuously records all ARP activities in the LAN. All inbound ARP packets are taken by the program along with accompanying address information and stored in a central database. If older entries are found that don’t match the data currently being sent, the program sends an email warning to the administrator. The procedure is effective, but is only suitable for networks with static IP addresses. If LAN IPs are distributed dynamically over a DHCP server, any change in the IP/MAC mapping results in a false alarm.
- ARP-Guard: ARP-Guard from the company ISL also monitors the internal network and relies on two different sensors. The LAN sensor works similarly to Arpwatch, analyzing inbound data packets and sounding an alarm in case of any discrepancies. The sensor management architecture of the software also has an SNMP sensor, which uses the Simple Network Management Protocol (SNMP) to access devices connected to the LAN and read out their ARP tables. In this way, not only are ARP attacks localized and warded off; the integrated address management also allows administrators to detect unwanted devices and prevent them from accessing the network.
- XArp: The XArp software relies on both active and passive modules to protect a network from ARP spoofing. The passive modules analyze ARP packets that are sent on the network, and match the accompanying address assignment with older entries. If discrepancies are noticed, the program alarm sounds. The control mechanism is based on statistical analyses and checks the network traffic on the basis on of various patterns which, according to developers, indicate ARP attacks. The sensitivity of this traffic filter can be adjusted gradually. The active modules of the software send their own packets into the network, in order to validate the ARP tables of the accessible devices and to fill them with valid entries.
The intrusion detection system (IDS) Snort also operates using an integrated arpspoof preprocessor, which enables it to monitor data traffic in the network and manually compile comparison lists. But this is comparatively expensive.
More importantly, IDS is mostly only used for the transition to external networks. Whether the use with the LAN counts must be decided on an individual basis. Occasionally such measures are opposed by the works council. An administrator who monitors the network via IDS has access to the entire network and so can also monitor all activities of the company’s employees – as a result, the control function is available but generally not desired.