Ping of death
The ping of death is an attack on a computer system, which can cause vulnerable systems to freeze or crash. Fortunately, since 1998 these kinds of attacks have no longer been possible on most devices.
Ping of death attacks use the Internet Control Message Protocol (ICMP), but in theory other IP-based protocols could be used as well. Since modern systems are secured against the ping of death, today’s malicious hackers tend to use a ping flood for attacks.
What is a ping of death?
A ping of death is a Denial of Service (DoS) attack. To start the attack, one sends a malicious data packet to the target. When the data packet is processed by the target system, the system encounters an error that causes it to crash.
Conceptually, the ping of death is comparable to a mail bomb: If the recipient opens the package, a mechanism is activated and the target is attacked and in the worst case destroyed. The ping command, from which the attack gets its name, is usually used to test whether a network is reachable. It’s based on the Internet Control Message Protocol (ICMP), which is used to communicate status information on the Internet.
There are various attacks that fall under the umbrella of denial of service attacks. The ping of death and SYN flood are both protocol attacks. In addition, there are also attacks on the application layer, for example HTTP floods. And lastly, volumetric attacks inflict damage by flooding their target with a stream of data. They include ping floods as well as UDP floods.
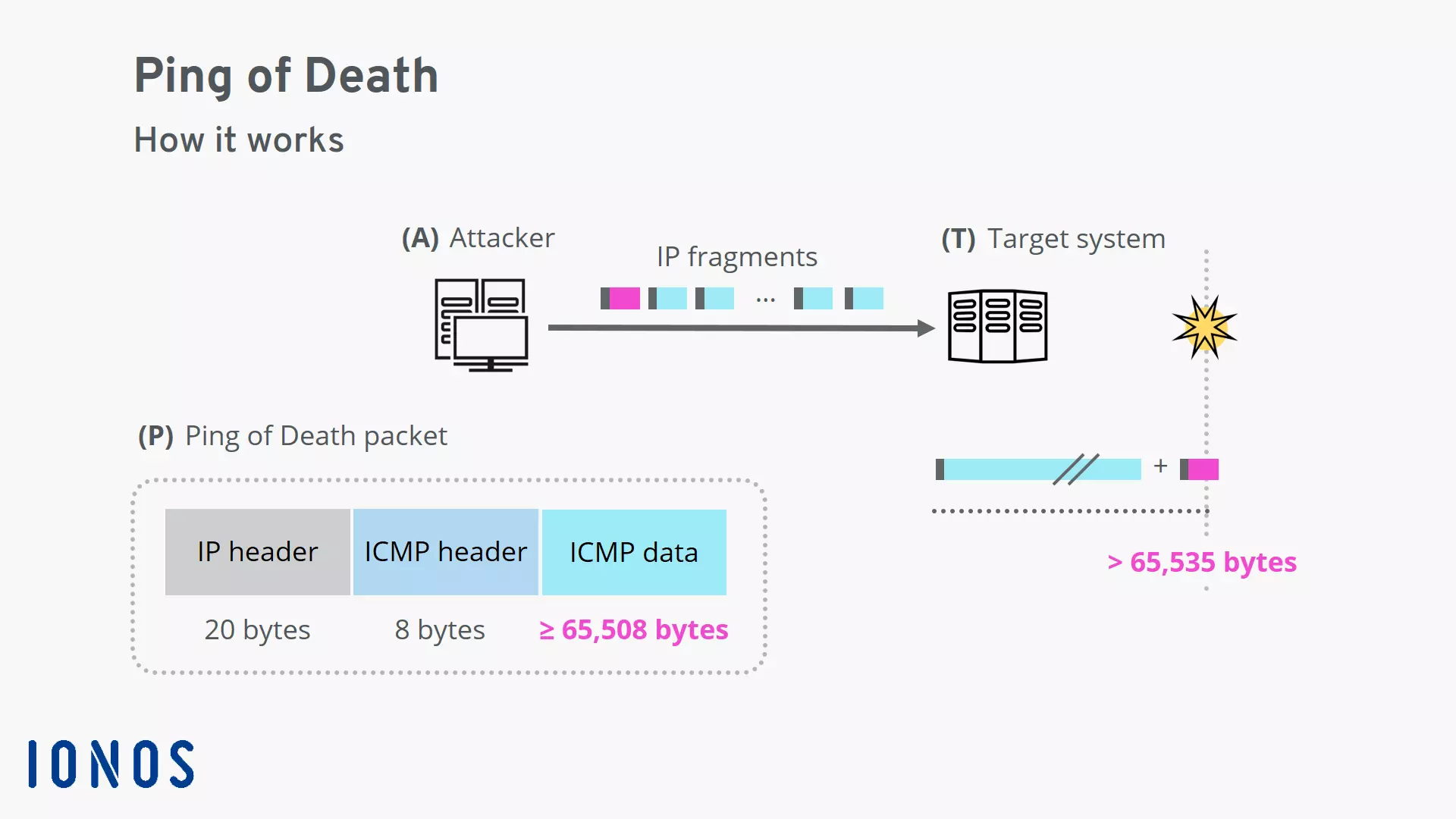
How a ping of death works
To carry out a ping of death attack, one first creates an ICMP packet that’s larger than allowed. The packet is broken down into smaller pieces for transport. Then, when it’s being put back together on the receiver side, the maximum allowed size is exceeded. In unprotected systems, this will lead to an overflow in the memory buffer, causing the system to freeze or crash.
A typical ICMP “echo” packet has a size of 56 bytes. In contrast, a ping of death packet has a size around 65,535 bytes, making it more than a thousand times larger. The limit of 65,535 bytes per packet comes from the underlying Internet Protocol (IP).
The attacker will use the ping command on the command line to create a ping of death packet. The options parameter is crucial, as its value establishes the size of the ICMP data field. On Windows systems, the option is found under “-l” for load. On other systems, the option is found under “-s” for size.
Ping of death on Windows:
ping <ip address> -l 65500 -w 1 -n 1Ping of death on Linux/UNIX/macOS:
ping <ip address> -s 65500 -t 1 -n 1Protecting yourself from ping of death attacks
The ping of death is an attack of the past. Since the attack was discovered in 1997, adjustments were made to server software and operating systems to provide protection against it. Additional checks ensure that the maximum size for packets isn’t exceeded when putting IP fragments together. Alternatively, the use of a larger memory buffer can help protect against the dreaded buffer overflow. With these measures in place, most systems are no longer vulnerable to the ping of death.
Furthermore, malicious packets are already filtered out by the network. This can happen on the level of routers and firewalls or be taken care of with a content delivery network (CDN). The IP header of each IP fragment is examined; each fragment must meet the requirement that “Fragment Offset + Total length ≤ 65.535 Bytes”, otherwise the packet is rejected.
Since modern systems are secured against the ping of death, these attacks no longer pose a threat for today’s users.