How to create a DKIM record
All reputable email servers try to block emails that are sent from forged sender addresses. One way to verify the authenticity of the sender is to use DKIM (DomainKeys Identified Mail), a method that allows you to digitally sign emails.
What is DKIM?
DKIM is an email authentication method that is carried out between the outbound and inbound mail server. This authentication process happens without the end user being aware that it’s happening.
Put simply, in DKIM, the outbound mail server attaches a digital signature to an email. The inbound server verifies the signature attached to the email by looking up the public key and then comparing it with the signature from the specified outgoing mail server.
If the public key does not match the signature, it may be due to one of the following reasons:
- The email was not sent from the mail server specified in the email header but was sent from another (fraudulent) server instead.
- The email was changed in transit to the recipient. For example, a hacker could intercept an email that was sent from a valid mail server, change it and then resend it.
How does DKIM work?
In order to understand DKIM, it’s best to take a look at the fundamental components that make it up. Below we’ve provided brief explanations of the three pillars of DKIM records.
Hashing
Using an algorithm, a unique sequence of characters is created from the contents of the email. This sequence of characters is known as the hash value and is placed in the header of the email. If the recipient of the email uses the same algorithm, they should get the same exact sequence of characters that is in the header of the email they have received. If the hash value isn’t identical to the one in the header, the recipient will know that the email has been changed.
Hashing is based on the same principle as the check digit on a bank deposit slip. Here, a value is calculated from the digits of the reference number and is added as the last digit of the reference number.
Asymmetric encryption
In order for the recipient to be sure that the hash value actually comes for the original sender, another step is necessary: a digital signature.
To authenticate senders, asymmetric encryption is used. This authentication process is based on a key pair: something that is encrypted with key A can only be decrypted with key B. One key is kept private (private key), while the other is made public (public key).
For more detailed information on encryption, have a look at our overview of encryption methods.
The encryption process looks like this:
- The sender encrypts the calculated hash value with the private key.
- The encrypted hash value is added to the email header as a digital signature.
- The receiver decrypts the signature by looking up the sender’s public key on the sender’s DNS server.
- The recipient then checks the decrypted hash value. If the hash value calculated by the receiver matches the decrypted one, then everything is okay.
TXT record on the name server
In order for an inbound mail server to retrieve the sender’s public key, the key must be published as a TXT record in the domain’s DNS zone.
To support this, the DKIM record contains the following elements:
- The version, often encoded with
v=DKIM1 - The encryption algorithm, which is always RSA (
k=rsa). - The public key (
p=); which is a long string. - The selector, which differs according to provider. Example:
default._domainkeyork1._domainkey
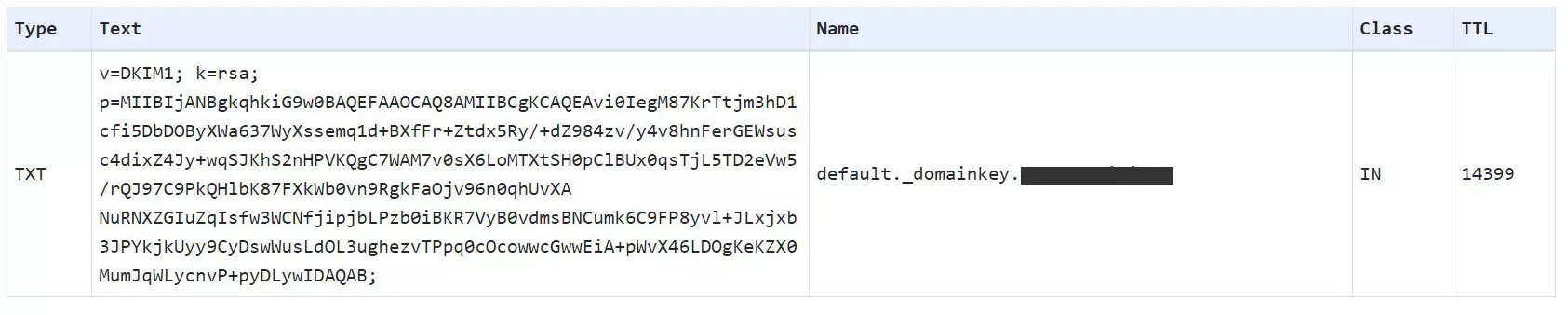
The DKIM record can usually only be retrieved using the email header. Both the domain name and the selector are required for the lookup. The selector is usually not known or is too time-consuming to find.
How to generate a DKIM key pair
To set up DKIM for your emails, you’ll need to start by getting a key pair. Typically, you can request a key pair from your email provider. If you operate you own mail server, you can generate the keys and entries required for DKIM yourself.
Request DKIM keys from an email provider
Email providers determine the process for requesting DKIM keys and, as a result, this can vary among providers. Keep in mind that some providers do not include DKIM support in all of their plans, with some only offering DKIM for business customers. Generally, you can request DKIM keys in the account settings or the management console provided by your email service provider. If you are not able to locate this option in your settings or management console, don’t hesitate to contact your provider’s customer support team in order to get help.
- 2 GB+ storage
- Sync across all your devices
- Spam filter and ad-free
Generate DKIM keys manually
You can manually generate the RSA key pair required for creating a DKIM record. Various tools for creating the RSA key pair are available online for free such as the DKIM Record Generator by EasyDMARC.
First, you’ll need to come up with a name for the selector (for example, k1). Enter this in along with the domain you want to use. Then, specify the key length that you would like to have. The generator will then provide you with a private key and a public one. The private key must be stored on the mail server. This can only be done by your mail provider. The public key, on the other hand, is stored in the DKIM record.
How to create a DKIM record
Once you have created your DKIM key pair, the keys need to be stored in the correct locations. In the case of the private key, this is the mail server. For the public key, this is the DNS entry for your domain. If your email provider generated the key pair, they most likely have already stored the key on the mail server.
If you operate your own mail server, you’ll need to store the private key yourself. The process for doing so varies and depends on which MTA (mail transfer agent) you are using.
To publish your public key, you need to create a DNS TXT in your domain to store the key in. To do this, follow the steps below:
- Log in to the admin area of your domain.
- Go to the DNS records section.
- Create a new DNS entry using the “TXT” type.
- In the Hostname field, type in your DKIM hostname. This consists of your selector and domain and is formatted like this:
selector._domainkey.exampledomain.com. In place ofselectorundexampledomain.com, use the selector name that was created when generating the key pair, and your domain name. - Enter the public key into the Value field.
- Save the new entry and wait for your DNS changes to be updated (This can take up to 2-3 days.)
How to check DKIM
To check if DKIM has been set up correctly, you can use a DKIM checker such as DKIM Record Lookup by EasyDMARC.
Another way you can check for the DKIM is by sending yourself an email and then looking at the header. Here you should see the entry “DKIM-Signature: ”.
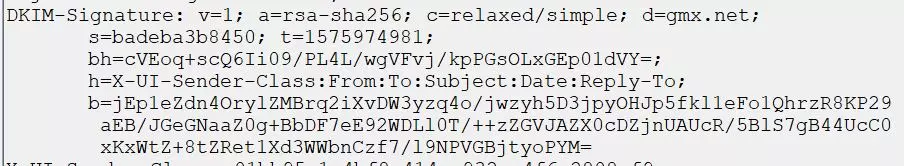
You can copy the header to the header analyzer tool from MX Toolbox to view clearer, more detailed information about the email header.

